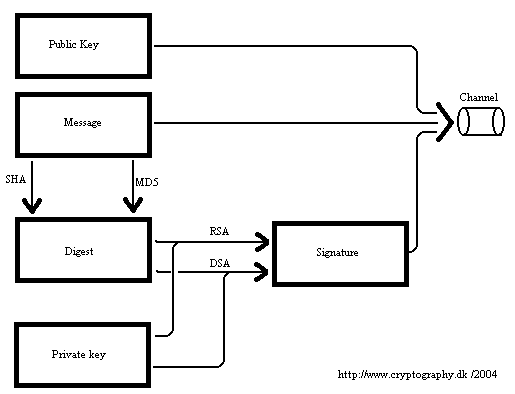
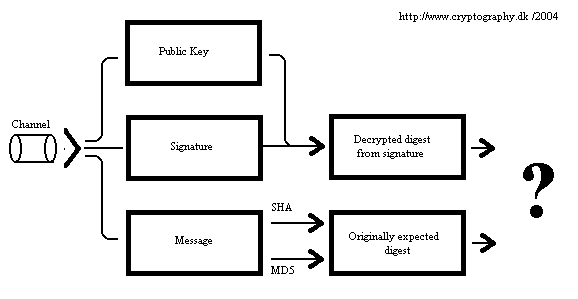
package dk.cryptography;
import java.security.KeyPairGenerator;
import java.security.KeyPair;
import java.security.PublicKey;
import java.security.PrivateKey;
import java.security.Signature;
import java.io.FileInputStream;
import java.io.File;
public class DigitalSignatureSimpleEncryption {
public static void main(String[] unused) {
try {
// Generate a key-pair
KeyPairGenerator kpg = KeyPairGenerator.getInstance("DSA");
kpg.initialize(512); // keysize is 512 bits
KeyPair kp = kpg.generateKeyPair();
PublicKey pubk = kp.getPublic();
PrivateKey prvk = kp.getPrivate();
String dataFileName = "DigitalSignatureSimpleEncryption.java";
byte[] signaturebytes = sign(dataFileName, prvk, "SHAwithDSA");
System.out.println("Signature(hex, length="+signaturebytes.length+"):" +
byteArray2Hex(signaturebytes));
boolean result = verify(dataFileName, pubk, "SHAwithDSA", signaturebytes);
System.out.println("\nSignature Verification Result = " + result);
}
catch(Exception ex) {
ex.printStackTrace();
}
}
private static byte[] sign(String datafile, PrivateKey prvKey,
String sigAlg) throws Exception {
Signature sig = Signature.getInstance(sigAlg);
sig.initSign(prvKey);
File f;
FileInputStream fis = new FileInputStream(f=new File(datafile));
byte[] dataBytes = new byte[(int)f.length()]; //small file - read all
int nread = fis.read(dataBytes); //hopefully nread==fis.length()
fis.close();
sig.update(dataBytes, 0, nread);
return sig.sign();
}
private static boolean verify(String datafile, PublicKey pubKey,
String sigAlg, byte[] sigbytes) throws Exception {
Signature sig = Signature.getInstance(sigAlg);
sig.initVerify(pubKey);
File f;
FileInputStream fis = new FileInputStream(f=new File(datafile));
byte[] dataBytes = new byte[(int)f.length()]; //small file - read all
int nread = fis.read(dataBytes); //hopefully nread==fis.length()
sig.update(dataBytes, 0, nread);
return sig.verify(sigbytes);
}
private static String byteArray2Hex(byte[] byteArray){
StringBuffer sb = new StringBuffer();
for (int i = 0; i < byteArray.length; i++){
String hex = Integer.toHexString(255 & (int)byteArray[i]);
sb.append( ((i%8)==0 ? "\n " : " ")
+ (hex.length()<2 ? ("0"+hex) : hex));
}
return sb.toString();
}
}